TR2009-026
On Information Leakage During Secure Verification of Compatibility Between Signals
-
- , "On Information Leakage During Secure Verification of Compatibility Between Signals", Canadian Workshop on Information Theory (CWIT), May 2009, pp. 75-78.BibTeX TR2009-026 PDF
- @inproceedings{Sun2009may,
- author = {Sun, W. and Rane, S.},
- title = {{On Information Leakage During Secure Verification of Compatibility Between Signals}},
- booktitle = {Canadian Workshop on Information Theory (CWIT)},
- year = 2009,
- pages = {75--78},
- month = may,
- isbn = {978-1-4244-3400-8},
- url = {https://www.merl.com/publications/TR2009-026}
- }
- , "On Information Leakage During Secure Verification of Compatibility Between Signals", Canadian Workshop on Information Theory (CWIT), May 2009, pp. 75-78.
-
Research Area:
Information Security
Abstract:
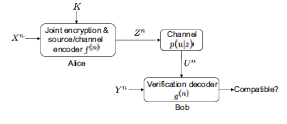
We consider a secure verification problem in which Alice wants to verify whether her signal Xn is compatible with Bob's signal Yn, where Xn and Yn are drawn i.i.d. according to a joint distribution p(x,y). The notion of compatibility is defined as the requirement that p(x,y) belongs to a certain set A of allowable joint distributions. For privacy, Alice jointly encrypts and encodes Xn and transmits the result over a public channel to Bob. Using the information leaked by the encryption algorithm, Bob verifies the compatibility of Xn with Yn. We characterize the minimum information that Alice's encryption and coding algorithm must leak in order to guarantee reliable verification results. Further, we determine the maximum information that Bob can hope to extract about Xn if he is curious. It is shown that a source/channel separation theorem holds for this scenario.
Related News & Events
-
NEWS CWIT 2009: publication by Wei Sun and Shantanu Rane Date: May 13, 2009
Where: Canadian Workshop on Information Theory (CWIT)
Research Area: Information SecurityBrief- The paper "On Information Leakage during Secure Verification of Compatibility between Signals" by Sun, W. and Rane, S. was presented at the Canadian Workshop on Information Theory (CWIT).